What is Phishing? Definition, types of attacks & more
Phishing is one of the oldest and most persistent forms of cyber attack, and in 2026, it’s more convincing and dangerous than ever.
Despite decades of awareness campaigns and security investment, phishing remains one of the most effective tactics in a cybercriminal’s playbook. The tactics have evolved rapidly thanks to AI, deepfake technology, and vast pools of breached data now used to target victims.
The tactics have evolved rapidly thanks to AI, deepfake technology, and vast pools of breached data now used to target victims. In 2025, phishing scams resulted in $13.7 million in financial losses in Australia alone, and this figure is expected to continue growing.
What is phishing?
Phishing is a form of social engineering that involves deceiving people into revealing sensitive information or installing malware.
At its core, phishing is about deception. Attackers impersonate trusted people or organisations to trick victims into sharing passwords, approving payments, or clicking on malicious links.
Phishing attacks exploit human psychology by using social engineering techniques to manipulate victims into revealing sensitive information or taking action before they verify what’s happening.
Why phishing still works
Despite decades of awareness campaigns and security investment, phishing remains one of the most effective tactics in a cybercriminal’s playbook. That’s because it preys on three powerful factors: human psychology, technological advancement, and the sheer volume of leaked personal data now available online.
-
Emotional manipulation works
Phishing attacks exploit human psychology by using social engineering techniques to manipulate victims into revealing sensitive information. Phishing messages often evoke strong emotions like fear, greed, and curiosity to manipulate victims into compliance.
These attacks rely on urgency, fear, curiosity, or authority to trick users into taking action, such as clicking a link, opening an attachment, or handing over credentials. When urgency is framed as a missed payment, a legal threat, or an internal HR issue, people often act before they think.
-
Technology is helping attackers, too
With the rise of AI, attackers can now generate near-perfect emails that mimic tone, branding, and even writing style. Deepfake voice and video make impersonation far more convincing than in years past, meaning traditional cues like spelling errors or awkward grammar are no longer reliable red flags.
AI-generated phishing involves creating highly personalised and grammatically perfect messages tailored to specific roles or industries. As of 2026, phishing attacks have become significantly more sophisticated through the use of generative AI.
-
Breached data is fuelling precision
Thanks to years of global data breaches, attackers now have access to billions of real email addresses, passwords, and personal details. This allows them to craft highly targeted spear phishing campaigns that feel credible because they often include accurate information about the recipient.
Phishing attacks are often more successful when they are personalised, using information gathered from social media or previous breaches. Attackers craft phishing messages, including deceptive emails, texts, or other communications, designed to trick victims into revealing sensitive information or clicking malicious links.
 Types of phishing attacks
Types of phishing attacks
While the basic concept of phishing has stayed the same, the tactics employed by cyber criminals have evolved with time. With advancements in technology, these attacks are quickly becoming more realistic. A phishing attack often follows a strategic lifecycle designed to exploit human psychology.
According to the Australian Cyber Security Centre (ACSC), 91% of cyber attacks in 2024 started with a phishing email. That means protecting your inbox isn’t just important, it’s critical.
Here are six of the most dangerous types of phishing scams we’re seeing today, plus how to spot them and stay protected.
1. Deepfake phishing attacks
What it is: Attackers use AI-generated audio or video to impersonate executives and request sensitive actions like payments or file access.
Who it targets: Finance teams, legal departments, and executive assistants.
How to recognise it: Unusual requests delivered via voice message or video, often with urgency or emotional appeal.
Prevention tips:
-
-
Always verify sensitive requests through a secondary channel
-
Use voice verification or biometrics for high-risk approvals
-
Don’t rely on caller ID or voice alone
-
2. AI-Powered spear phishing
What it is: AI-driven attacks that craft highly personalised messages using scraped data. This is known as spear phishing, where personalised messaging is used to trick a specific individual or organisation into believing the communication is legitimate.
Who it targets: Executives, high-profile individuals, employees with public-facing profiles, and IT administrators. Whaling is a variant of spear phishing that specifically targets senior leaders.
How to recognise it: Emails that seem unusually relevant or written in your tone or style, but sent from unfamiliar addresses.
Prevention tips:
-
-
Conduct ongoing phishing simulations and training
-
Use email filtering with AI threat detection
-
Enforce MFA to reduce account takeover risks
-
3. Extortion emails
What it is: Scammers claim to have compromising information or footage and demand a ransom to prevent its release.
Who it targets: Anyone, but often individuals with exposed credentials from previous breaches.
How to recognise it: The email is sent from a spoofed version of your address and includes personal data such as old passwords.
Prevention tips:
-
-
Don’t engage or respond
-
Change passwords immediately
-
Report to the IT or security team and delete the message
-
4. Business email compromise (BEC)
What it is: Attackers impersonate a trusted internal party like the CEO or CFO to initiate fraudulent transactions or steal sensitive data.
Who it targets: CFOs, finance teams, HR, and executive support.
How to recognise it: Last-minute payment requests, banking detail changes, or urgent messages that bypass standard processes.
Prevention tips:
-
-
Use approval workflows and dual verification for payments
-
Executives and finance staff on BEC tactics
-
Monitor for domain spoofing or lookalike domains
-
5. Smishing & vishing
What it is: Phishing via SMS (smishing) or voice calls (vishing). Messages often impersonate a financial institution, logistics firms, or internal IT teams.
Who it targets: Mobile users, especially in hybrid/remote work environments.
How to recognise it: Short messages with suspicious links, caller impersonations, or requests for sensitive information.
Prevention tips:
-
-
Don’t click links in unsolicited SMS messages
-
Verify all voice requests, especially those involving credentials or access
-
Use mobile threat detection software if available
-
6. Clone phishing
What it is: A legitimate email is copied, the content is modified with malicious links or attachments, and then resent to the original recipient list.
Who it targets: Anyone receiving repeat emails, especially in finance, logistics, or support roles.
How to recognise it: Duplicate emails with slight changes in links, formatting, or sender details.
Prevention tips:
-
Check links before clicking, hover to verify destinations
-
Be wary of repeat emails with modified attachments
-
Use email authenticity tools such as DMARC, SPF, and DKIM
Real-World Examples
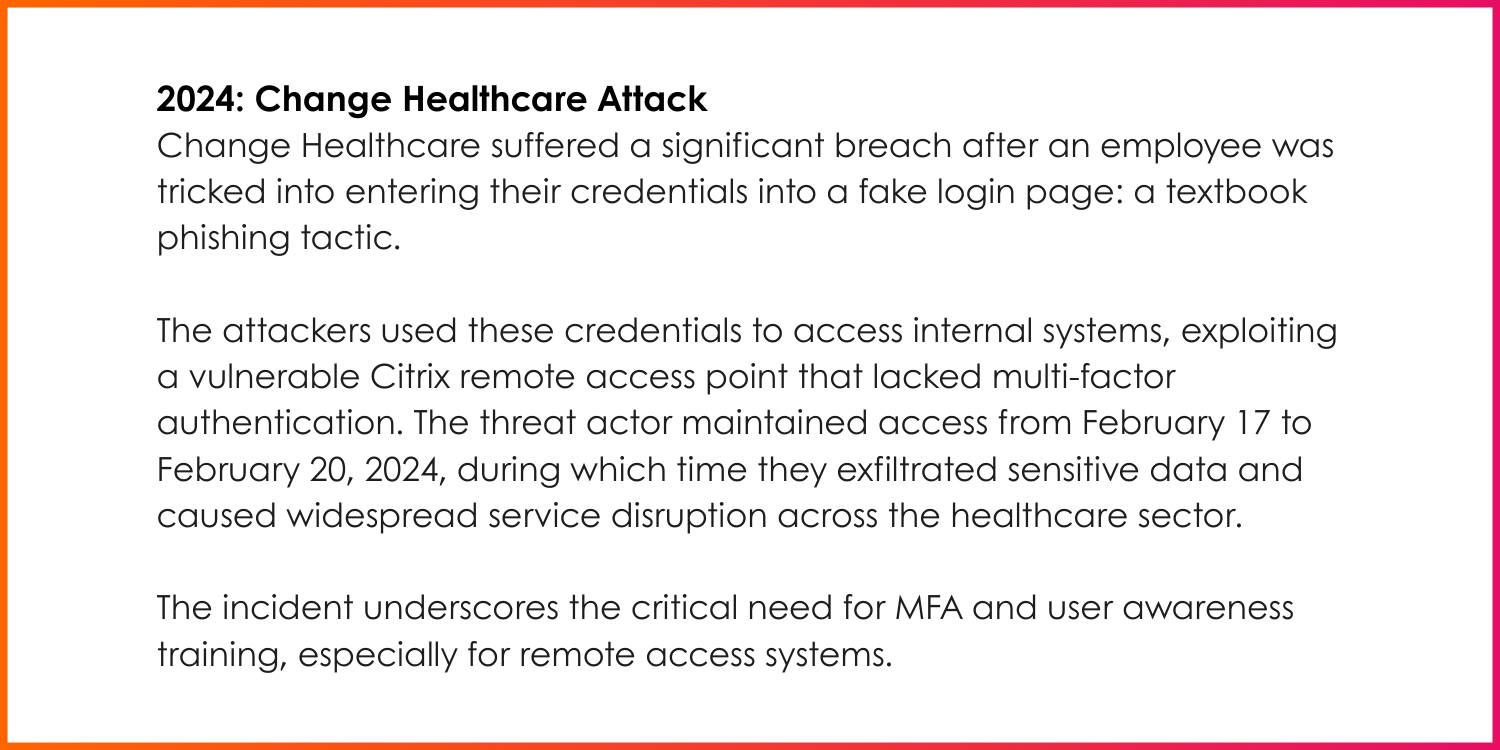
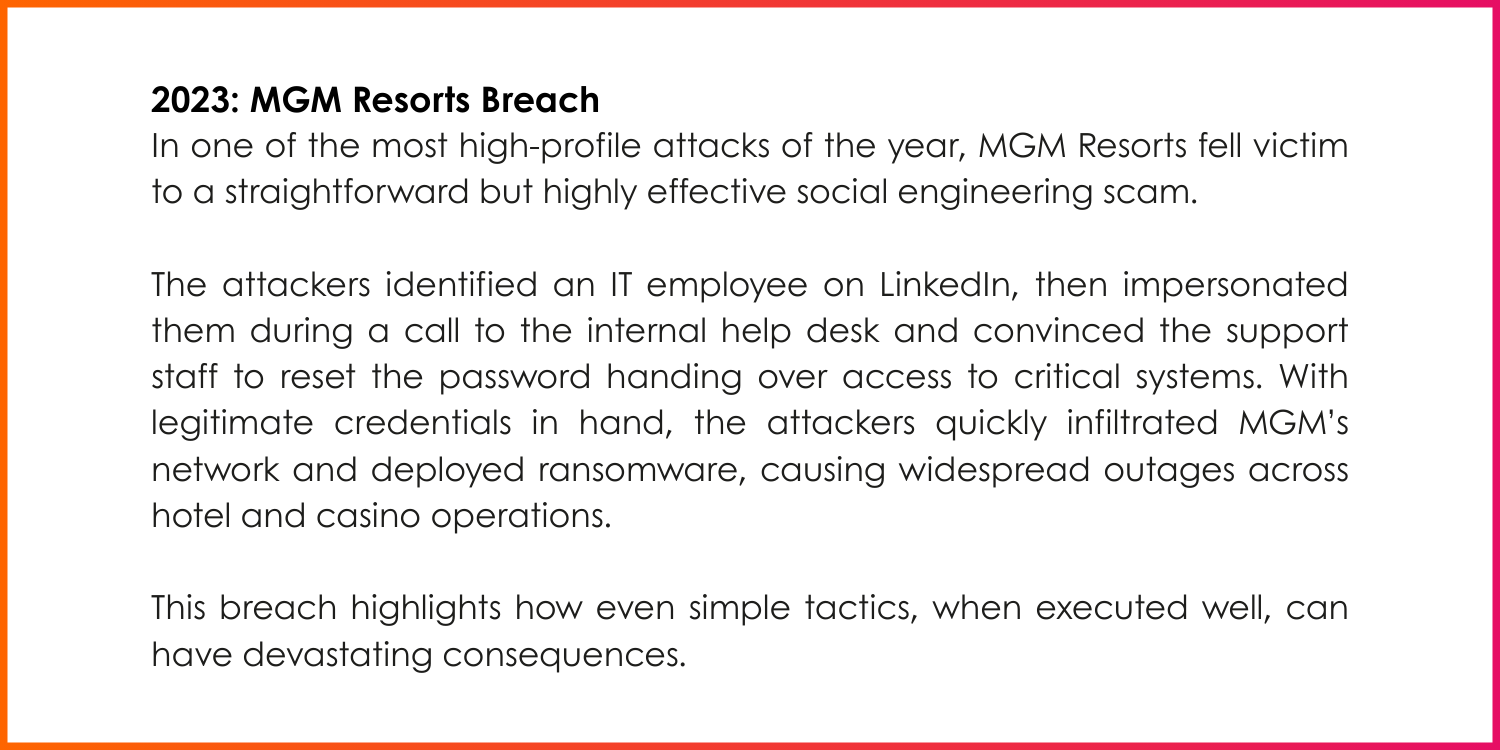
How to protect your business from phishing
Phishing threats are increasing in sophistication and volume, but with the right tools, training, and policies, you can significantly reduce your exposure.
AI-driven phishing detection solutions can proactively identify and block phishing threats by analysing language patterns and suspicious behaviours in real time, providing an essential layer of defence for organisations.
Build the right tech stack
-
-
Deploy advanced email filtering and threat detection solutions
-
Implement DMARC, SPF, and DKIM to verify legitimate senders
-
Use MFA across all critical systems to block unauthorised access
-
Monitor for credential leaks and suspicious login activity with SIEM tools
-
Invest in ongoing training
-
-
Run regular phishing simulations to build user awareness
-
Train staff to spot social engineering red flags
-
Tailor sessions for high-risk teams like finance, HR, and exec support
-
Create strong policies and response plans
-
-
Define clear protocols for reporting phishing attempts
-
Document your incident response plan and test it regularly
-
Establish approval workflows for financial transactions and sensitive data access
-
A strong phishing defence isn’t built overnight, but consistent, layered protection will make a measurable difference.
The cost of inaction
Failing to prepare for phishing attacks can have wide-reaching consequences, not just financially, but operationally and reputationally.
Successful phishing attacks can lead to identity theft, credit card fraud, monetary theft, extortion, account takeovers, and even espionage.
Prevention is far less costly than recovery. Investing in layered defences today protects your bottom line tomorrow.
Staying one step ahead
Phishing attacks are evolving, and so should your defences.
At The Missing Link, we don’t just react to threats. We help you stay ahead of them with a strategic, layered approach to cyber security.
Get in touch to strengthen your defences and ensure your business is protected against the phishing threats of today and tomorrow.
Author
As a Content Marketing Specialist at The Missing Link, I turn technical insights into engaging stories that help businesses navigate the world of IT, cybersecurity, and automation. With a strong background in content strategy and digital marketing, I specialise in making complex topics accessible, relevant, and valuable to our audience. My passion for storytelling is driven by a belief that great content connects, educates, and inspires. When I’m not crafting compelling narratives, I’m exploring new cultures, diving into literature, or seeking out the next great culinary experience.
