Security in our digital world is paramount, and for businesses using Microsoft 365 (M365), understanding potential pitfalls in security settings is crucial.
When setting up M365 tenancies, several default settings are applied which can, unintentionally, create avenues for security breaches. While Microsoft does its part to review and refine these default settings over time, older tenancies might still be vulnerable due to overlooked or legacy configurations.
As IT service experts, we've seen a pattern when carrying out M365 Security Reviews. There are consistent misconfigurations we regularly encounter across the board.
Let’s discuss the top five we've identified and what you can do to address them.
The importance of MFA cannot be overstated. It significantly reduces the likelihood of identity theft, ensuring that even if passwords are compromised, they cannot be utilised without the second authentication factor. We often spot MFA enabled only for a few accounts, leaving a glaring security gap.
Recommendation: Utilise conditional access policies to guarantee MFA is active for every user. This ensures comprehensive protection, with no account left exposed.
2. Apply MFA for privileged accounts without exceptions
The stakes are even higher for privileged accounts, which typically have access to more extensive permissions than standard ones. A breach into one of these accounts can have wide-reaching implications.
Recommendation: Similar to regular accounts, always ensure MFA is enforced for privileged accounts. Using conditional access policies will ensure that not a single privileged account is left without this crucial security layer.
3. Regulate external sharing on SharePoint sites
By default, external sharing is enabled for all SharePoint sites, posing a risk of unintentional or even intentional sharing of confidential data.
Recommendation: External sharing should only be permitted on designated and actively managed SharePoint sites meant for this purpose. All other sites should default to internal sharing only to safeguard sensitive information. Security should be further strengthened by also enforcing appropriate sharing policies.
4. Adjust default sharing settings for SharePoint and Teams
Sharing is at the heart of collaborative work. However, the balance between security and functionality is delicate. Default settings can lead to unintentional sharing of confidential files or even granting unwanted editing permissions. Default sharing settings include:
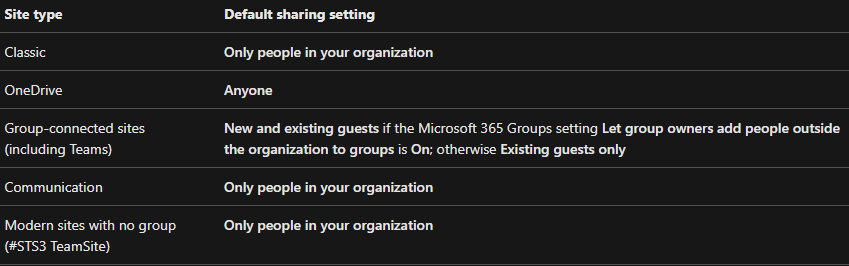
Source: Microsoft
Recommendation: Modify these default sharing settings at the highest level possible. Ensure that resources can only be shared by authorised individuals and that sharing permissions are appropriately restricted. Adopting a "least privilege" approach is also advisable, where only the necessary minimum permissions are granted. You should also ensure that these settings are reviewed on a regular basis, and when individuals are offboarded.
5. Enable account lockout protection
By default, M365 operates its password protection in what's termed as "audit mode", rather than a more stringent enforcement. This functionality permits policies that can lock a user's account after a series of unsuccessful login attempts. Moreover, it offers the ability to create a bespoke list of prohibited passwords.
Recommendation: Transition from the "audit mode" to the "enforced mode". Also, populate the prohibited password list with keywords, terminologies, and phrases that are relevant to your business. This simple change can significantly bolster your security with minimal effort.
Security isn’t static. As threats evolve, so should your protective measures. While M365 offers unprecedented opportunities for productivity and innovation, it can inadvertently expose critical data without proper configurations. Ensuring that your M365 tenancies are well-configured is a significant step towards creating a robust digital fortress for your business.
Regularly review your settings, seek expert advice, and be proactive in your approach to safeguarding your company's digital assets. Remember, in the realm of cybersecurity, prevention is always better than cure. Generic setups may not always align with your industry's specific needs. That’s where we come in.
Contact our team today for an independent, third-party security review to ensure comprehensive protection tailored to your organisation.

